A “Zero Trust” Approach to Business Security: What It Is and Why It’s Critical Now
Introduction In today’s hyper-connected world, traditional perimeter-based security models are no longer enough. With employees working remotely, sensitive data stored…
Job Scams and Data Exploitation: A Hidden Threat to Your Business’s Reputation
Why Are Job Scams on the Rise? In today’s digital hiring landscape, job seekers and businesses alike are facing a…
The Quantum Computing Threat: Why Your Encrypted Business Data Isn’t Safe Forever
Introduction: Why Worry About Quantum Computing Now? For decades, encryption has been the foundation of digital security. Businesses trust encryption…
Building a Culture of Fraud Awareness: Empowering Your Employees as the First Line of Defense
Fraud is no longer a distant concern—it’s a daily threat that can cripple businesses of all sizes. While advanced Business…
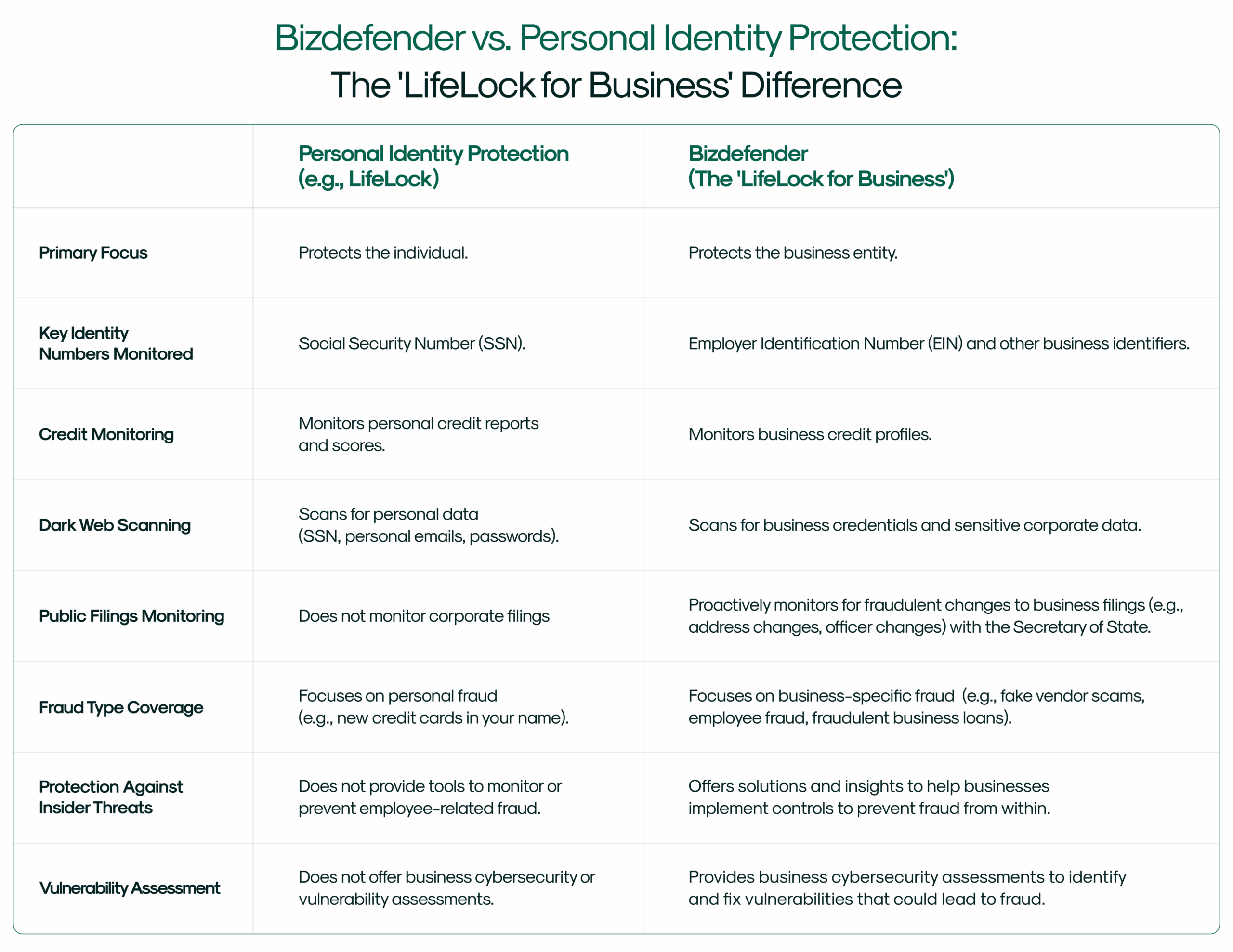
Bizdefender vs. LifeLock: The ‘Lifelock for Business’ Guide
When it comes to protecting against identity theft, LifeLock is a name almost everyone recognizes. For years, it has been…
Cybersecurity and Fraud: A Holistic Business Approach
For too long, businesses have treated cybersecurity and fraud prevention as two separate, siloed disciplines. Cybersecurity was the domain of…
Insider Threats: Protecting Your Business from Fraud Within
When most business owners think about fraud and security, their minds immediately turn to external threats—hackers, fake vendors, and online…
The Rise of Synthetic Identity Fraud: Protecting Your Business from This Evolving Threat
The digital age has brought unprecedented convenience and speed to business operations, but it has also opened the door to…
The Legal Landscape of Business Identity Theft: What You Need to Know
In an increasingly digital world, businesses face a constant barrage of threats, and among the most insidious is business identity…
Responding to the Unthinkable: A Business Identity Theft Recovery Checklist
The unthinkable has happened. You suspect your business has fallen victim to identity theft. The panic sets in, the questions…
Beyond Credit Monitoring: A Comprehensive Approach to Business Identity Theft Protection
In today’s interconnected world, the threat of business identity theft is more pervasive than ever. While many business owners wisely…
Is Your Business at Risk? Understanding How Business Identity Theft Happens
In today’s interconnected world, the threat of identity theft extends far beyond individuals. Businesses, from small startups to established enterprises,…